You’re only human. And criminals called social engineers, or “human hackers”, are out to manipulate you into revealing sensitive information or into downloading software that will compromise your computer’s security. Social engineering attacks can happen online, in-person, or through other interactions. How do they do it? They often impersonate legitimate organizations to gain trust, then play on your emotions—such as fear (‘Your grandson is in jail”), greed (“You’ve just won a million dollars!”), or sympathy (“I’m bankrupt due to medical bills—please wire money now!”) that will entice you to divulge your personal and financial data or click on a link that takes control of your computer system.
These fraudsters are smart and unrelenting. And incidents are skyrocketing. Research from 2024 shows hundreds of millions of threats come from information stealers, Trojans (that lure you to install malicious software, or malware), and ransomware (where your computer’s files are encrypted and the criminals demand a ransom payment to decrypt them). There are ways to outsmart them, but you first need to be aware of exactly how they operate.
The most common social engineering attacks that aim to deceive you:
Phishing: The cyberthief creates a sense of urgency (“24 hours before unclaimed funds expire!”) or appeals to your curiosity with a leading question (“Are you owed compensation?”) via emails, texts - called smishing, or phone calls. If you engage by giving personal information or click on an embedded link, they can gain access to your computer and bank accounts, credit cards, etc. government agencies, financial institutions, or popular social media applications or file sharing sites — to gain confidence and encourage you to follow the email’s directives, such as divulging sensitive information. These phishing attacks prey on curiosity, greed, great deals, and emotion
1. Baiting: Through emotional lures similar to phishing, they “bait” you into installing or clicking on something that ends up putting malware onto your computer system. Offers for gift cards, free smartphones, or even a share of a lottery winner’s profits — are popular baiting techniques.
2. Quid pro quo: Here, a criminal offers a seemingly desirable product or service in exchange for access to confidential information (“Here’s new software to make your computer run faster!” or “We think you’d be a perfect candidate for this job!”).
3. Pretexting involves bad actors impersonating someone you trust—your boss, a police officer, government official—so you feel obliged to respond and follow their directions to provide sensitive information; once you comply, they can access your financial accounts.
4. Scareware, like the name implies, frightens you with scary pop-ups and notifications (“Warning! Your computer may be infected!”), leading you to install malware that gives them access to your data. Examples can include pops up such as
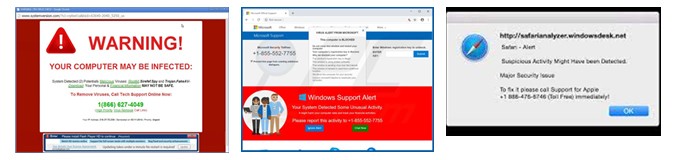
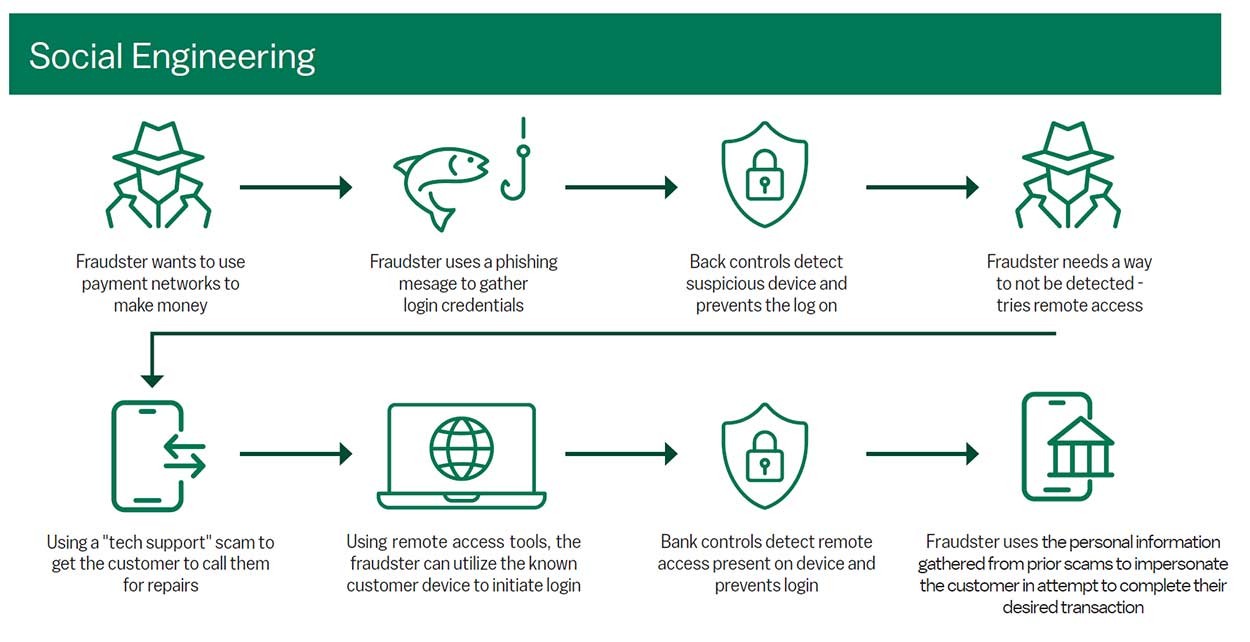
Fraud in motion: Learn the ways fraudsters try to access your information. It’s more than you think.
Even the most sophisticated computer users can be vulnerable to social engineering scams. The more aware you are of how scam artists work, the less likely you are to become a victim.
How to protect yourself
It can be intimidating to know that there are people who look to misuse your financial data. Just follow these guidelines to guard your personal information.
Security checklist
- Verify all requests for information from a source that’s unfamiliar or even if the name is familiar but something looks “off”—perhaps when you check the sender’s origin, it’s a personal or odd email address; or maybe the message has misspellings and grammar errors. Delete the email without responding and contact the actual company directly to report the message.
- Be password savvy. Make it a hard-to-guess mix of uppercase and lowercase letters, numbers, and symbols at least 12 characters long. Save the details in a password manager software “vault” application, enable multifactor authentication (MFA) on your accounts so you need a password and a one-time code, use different passwords across accounts, and never share your login credentials.
- Regularly update your operating system and antivirus software to ensure you have the latest security features (SPAM filter and a personal firewall), and check your online accounts for any unauthorized activity.
- Think before you click on embedded hyperlinks in emails or texts that look suspicious. Enter the URL into the address bar to see if it takes you to a reliable source. Still not sure? Call the supposed company sender to check its authenticity.
- Stick to private Wi-Fi online activity and don’t perform your banking, credit card, or other financial activities in a public place.
In such a fast-paced world, it’s tempting to quickly rush in and select a link or respond to an email that engages your attention. Armed with the information provided above, however, you will be far less likely to get caught in a fraudster’s trap and unwittingly reveal your valuable personal and financial information.
Have you been targeted by online fraudsters? Do the following:
- Contact M&T Bank immediately to investigate and help secure your account
- Immediately change the passwords on any accounts where you entered information in response to the social engineering incident.
- Freeze your credit or set a fraud alert with credit bureaus (Equifax, Experian, TransUnion).
- Monitor your financial accounts and contact your bank or card issuer right away if you notice any suspicious activity.